Exposure No. 05
Hacking the Hackers
This exposure stems from an in-depth investigation led by our Cyber Forensic Expert, Michael Szabó, who uncovered our target’s personal email address stemming from a dark web breach. Through covert techniques, we accessed associated platforms and obtained the password to unlock a wealth of communications and data, including exchanges from but not limited to the breached email account. We are publishing these findings in the public interest, given Stuart Collier's significant role in our Collier Exposed Investigative Project. All actions were conducted responsibly, in line with data protection laws and journalistic ethics, ensuring transparency and accountability while focusing on the public's right to know.
In the relentless pursuit of our target, the News of the World-era gutter journo, Stuart Collier, nothing has been off-limits in our relentless search for evidence. This includes securing access to all relevant communications, enabling a deeper investigation into Stuart Collier’s nefarious activities in and around Fleet Street, as well as his sadistic undertakings away from those press circles. The findings are being released as part of this Collier Exposed Investigative Project, serving to substantiate and support the evidence we are exposing about our sadistic investigative target.
The Breach: Gaining Access to Stuart Collier’s Accounts
We can now disclose that the breach provided direct access to the target's primary and private iCloud account: stuartcollieroxford@icloud.com. Stuart Collier’s closest associates can corroborate this as his primary account, used for their communications with him. By making this revelation public, we advance the Collier Exposed investigation and alert readers and the wider public to our access of the compromised email account.
The ramifications are far-reaching, not only tarnishing Stuart Collier’s public perception and legacy but also implicating those within his orbit drawn into the scope of this investigation. This critical breakthrough amplifies our findings, with corroborative evidence from his associates’ communications further solidifying the weight and credibility of our exposures.
Uncovering Key Communications: The Web of Stuart Collier's Associates
Our investigation unearthed a vast trove of confidential communications sent and received by this Murdoch-era news hack. Among the implicated figures—some yet to be disclosed—are Clive Goodman, News Corp’s notorious chief telephone hacker and Stuart Collier’s closest confidant, and Alex Marunchak, a fellow fraternity member and the former chief crime reporter at the now-defunct News of the World. Crucially, and setting the stage for a future exposé, Marunchak also served as the paper’s liaison to Daniel Morgan of Southern Investigations, who would soon fall victim to a brutal and still-unresolved murder—a crime in which Stuart Collier is implicated.
This web of connections further entangles Sid Fillery—a disgraced former police officer and convicted paedophile, whose computer was found to contain category A paedophilic images. Fillery was a primary suspect in Daniel Morgan’s murder, suspected of acting in collaboration with his alleged accomplice, Jonathan Rees. Through the breach, we uncovered a wealth of communications that not only expose these figures’ interactions but also cast a glaring light on Stuart Collier’s depraved and scandal-tainted career within Fleet Street’s shadowy corridors, as they frequently and in great detail reminisce about the “old times,” “the anything-goes days,” and their shared fraternity ties.
Password Cracking: A Breakthrough in the Investigation
Our initial breach of several online accounts linked to Stuart Collier’s close family circles yielded an abundance of invaluable information. Although many of these accounts eventually became dormant or inaccessible, they provided a digital blueprint of Stuart Collier’s life, enabling us to construct a comprehensive web of his activities. These breaches granted us access to personal details, live updates about his private life from his inner family circle, and even intimate photographs from his private settings—allowing us to monitor his movements, practically in real time.
This level of access extended beyond the digital realm, enabling us to conduct physical surveillance of Stuart Collier’s whereabouts. We tracked his movements in person, following him during outings and errands. Further details about this surveillance, including his activities at his private residence, will be shared in an upcoming journal entry.
One notable instance of our monitoring efforts included advance knowledge of Guardian journalist Simon Murphey’s visit to Stuart Collier’s residence in preparation for his 2019 interview regarding Stuart Collier’s role in the infamous Guppygate scandal. By intercepting their liaison communications, we gained additional insight into the preparation and context of this meeting.
Throughout this period, Michael Szabó, the Collier Exposed investigation’s Cyber Forensic Expert, continued to vigilantly identify and further exploit vulnerabilities in Stuart Collier’s personal online security, ensuring the integrity and widened depth of our investigation.
The Source of Exposure: The Dark Web
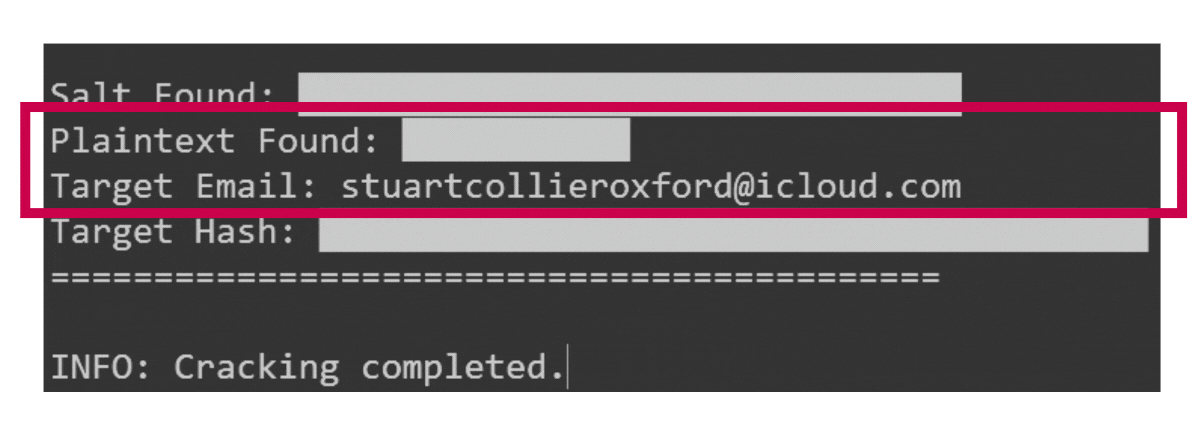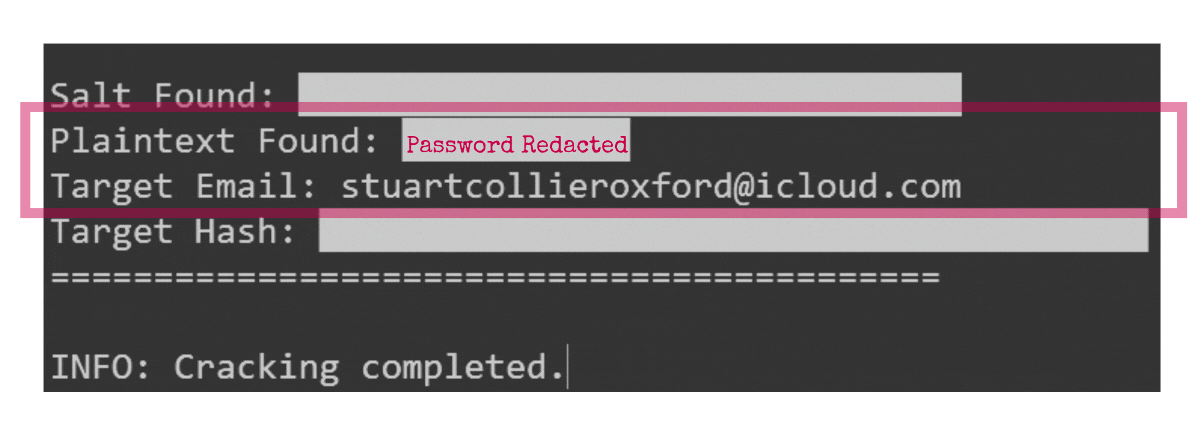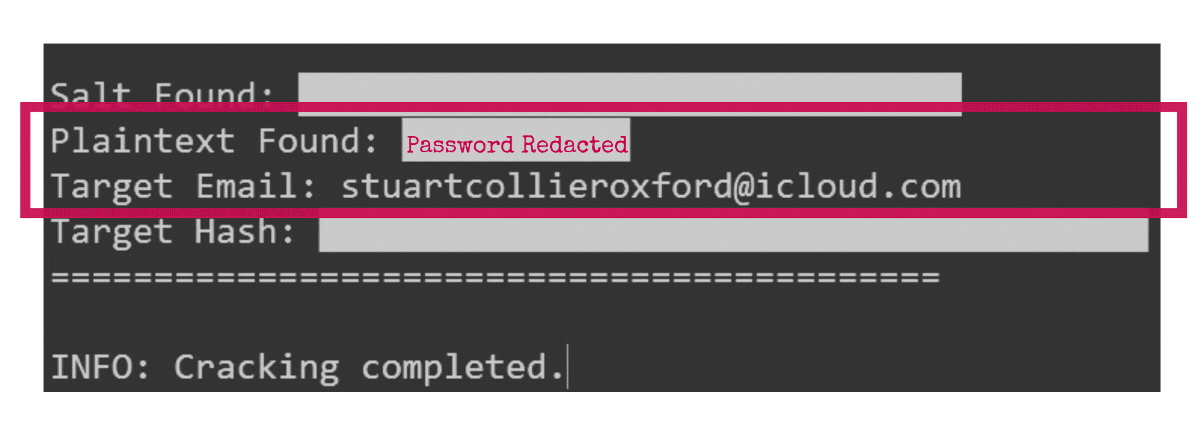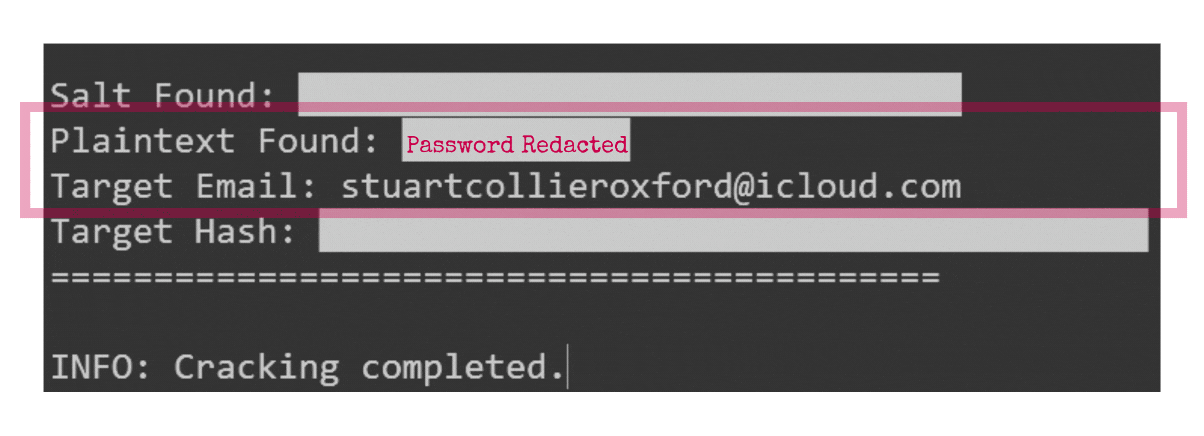
On the evening of Thursday, 18 January 2018, Michael Szabó, the Collier Exposed investigation’s Cyber Forensic Expert, received an alert about a dataset from a breach being touted on a dark web forum. The file, titled combos.vip-icloud.com.txt, contained a treasure trove of compromised data. Among the 3.6GB dataset—originally compromised on 26 October 2017 from MyHeritage’s servers, a popular genealogy and DNA-testing platform—was Stuart Collier’s email address. Accompanying this were its SHA1-hashed password and the critical salt (a cryptographic enhancement to password security).
The breach wasn’t publicly confirmed until 4 June 2018, when MyHeritage’s Chief Information Security Officer announced it had been compromised. This disclosure followed an alert from a security researcher using the email: benjaminblue@exploit.im. The breach affected millions of users, including Stuart Collier. His inclusion in the dataset marked the breakthrough we had been anticipating—it was only a matter of time.
Prior to this public acknowledgment, and acting in the public interest, we facilitated an anonymous cryptocurrency transaction to a dark web operative to acquire data specifically linked to Stuart Collier and several other individuals in his circle. While the dataset contained hashed passwords and their associated salts, the challenge of cracking these credentials required expertise. This is where Michael Szabó, our private cybersecurity consultant and acting Cyber Forensic Expert, played a pivotal role. Michael brings a unique perspective shaped by his own history in the UK press scene—a story involving our target that will be revealed in future investigative exposures.
To decrypt this barrier, Michael Szabó employed Hashcat, an industry-leading password recovery tool renowned for deciphering encrypted credentials, alongside other advanced tools and techniques. Armed with state-of-the-art technology and expertise, Szabó successfully cracked Stuart Collier’s password, achieving yet another pivotal breakthrough in the investigation.
This accomplishment represents the foundation of Exposure No. 05, which further exposes Stuart Collier—a Murdoch-era tabloid journalist entangled in the News of the World, among other scandals, not least its notorious Phone Hacking Scandal. In an ironic twist, we hacked the hackers, using their own methods but to reveal the truth.
Detailed Findings: The Extent of the Data Uncovered
With Stuart Collier’s password now decrypted and in plaintext, Michael Szabó initiated the next phase of the investigation. Remarkably, Stuart Collier exhibited a consistent and careless habit of reusing the same password across nearly all his online accounts. On the rare occasions where he deviated from this pattern, he employed a rudimentary variation system so predictable it barely qualified as a challenge, allowing access to his other online profiles with laughable ease.
This revelation significantly expanded the scope of our investigation, granting access not only to his primary email account but also to a wide array of additional online assets. These included email accounts of immediate family and close associates, social media profiles, cloud storage drives, location data, photo EXIF metadata, contact lists, browser history, device and application backups, utility service accounts, booking platforms, shopping sites, and numerous other sets of private data.
Collaboration and Transparency: Engaging with Fellow Investigators
Our investigation extended well beyond Stuart Collier alone, breaching not only the accounts of his family members and close associates but, more importantly, infiltrating his tabloid reporter circles. This included extensive access to a range of News International and News Corp email communications. Notable examples include recent exchanges with Rebekah Mary Brooks (née Wade; born 27 May 1968) at rebekahmbrooks@gmail.com, as well as her other personal email accounts. Brooks, the former editor of News of the World, CEO of News International, and Chief Executive Officer of News UK, remains a close associate of Rupert Murdoch and his son, James Murdoch. By accessing Stuart Collier's accounts, we traced his communications and uncovered incriminating exchanges in their original context.
We are currently collaborating with other investigative teams focused on the Murdoch press, specifically those investigating the News of the World phone hacking scandal. Our findings, which implicate several existing and new and high-profile members of the hacking ring, are deeply troubling. However, the sheer volume of data we’ve uncovered far exceeds the scope of our singular focus on Stuart Collier.
As of today, the compromised data we've collected on Stuart Collier and his associates includes:
17GB of communication data, primarily emails and instant messaging communications
75GB of electronic documentation, including DOC and PDF files from cloud storage drives
550GB of media content, including images and videos sourced from personal cloud storage drives
For those interested in collaborating with us to process and disseminate this extensive trove of material in the public interest, please refer to our investigation’s contact page for instructions on how to establish secure and, where necessary, anonymous communication.
Stuart Collier's Continued Carelessness: Repeated Vulnerabilities
Throughout this period, Stuart Collier remained blissfully ignorant of basic online security practices, failing to enable iCloud’s two-factor authentication (2FA)—a basic security measure that Apple made mandatory in 2019. By the time this was implemented, we had already skimmed and extracted every bit of data, leaving the breached accounts devoid of any further investigative value. Stuart Collier’s failure to adapt was telling—by then, he had become increasingly incoherent and irrelevant in his digital activities, prompting us to wind down our monitoring efforts.
Throughout the investigation, there was no indication that Stuart Collier ever became aware of our breaches, nor did he alter any of his online behaviour. He, along with others whose accounts were compromised, remained entirely oblivious to our actions. To compound his incompetence, he continued to create new online accounts using the very same password we had already cracked.
Securing the Data: Archiving and Safeguarding Information
After extracting all relevant data from Stuart Collier’s accounts, we securely archived it in our encrypted investigative file repository. This now forms part of our investigative dossier, which is available for public viewing here. Additionally, we are committed to forwarding any potentially illegal material to the relevant authorities for further investigation.
Right of Reply
In line with our commitment to transparency, a Right of Reply email was sent to the inbox associated with the deceased Stuart Collier, notifying those monitoring the account of our investigative access, while offering an opportunity to comment on his legacy. To verify this exposure, we will confirm the cracked password upon receipt of an email from the breached account (stuartcollieroxford@icloud.com). Our secure contact details are available here.

This email confirms that our investigation was conducted solely in the public interest and invites responses to ensure all perspectives are included.




